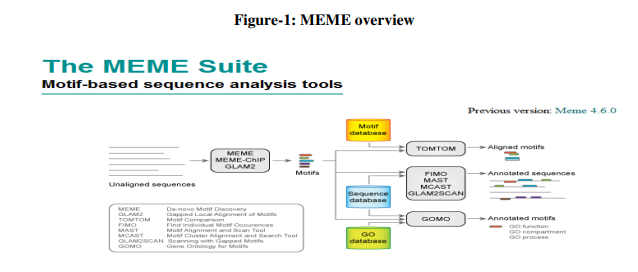
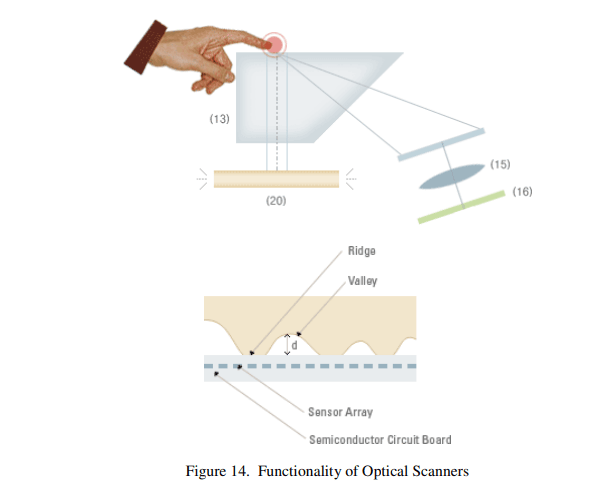
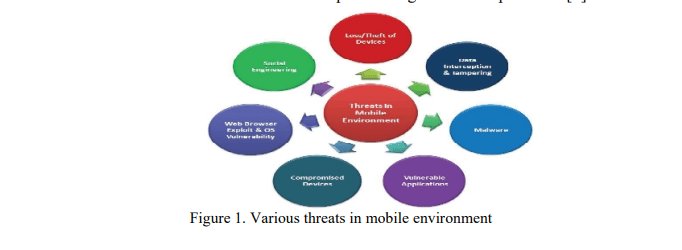
Geo-Ontology and Geographical Information System Extended by a first-order logic language: Application to malaria control
Guillaume Koum[1]Josiane Etang [2],[3]
[1] Département d’Informatique. Ecole Nationale Supérieure Polytechnique. B.P. 8390
Yaoundé, Cameroun
[2] Organisation de Coordination pour la lutte contre les Endémies en Afrique Centrale
B.P. 288 Yaoundé, Cameroun
[3] Faculté de Médecine et de Sciences pharmaceutiques. Université de Douala, B.P.
2701 Douala, Cameroun
c
Abstract
A geo-ontology can be built around a Geographic Information System (GIS) and enriched with a firstorder logic language under the closed-world assumption (CWA). This extended system provides knowledge representation formalisms that are aimed to describe general conceptual information. They can also be used in the construction of the knowledge base of a reasoning tool. In this paper an environment is defined where a geo-ontology offers possibilities with a system that allows users to represent and reason about some aspects of the real world. With respect to the added intelligence; knowledge is preserved and enhanced. Knowledge enhancement is performed under the CWA in a subset of the first-order logic language. A geo-reasoning task is undertaken so that a GIS and a geo-ontology are integrated in what can correspond to a natural language processing system. The framework is implemented to demonstrate geo-ontology’s ability to enhance knowledge in malaria control domain.
Keywords: geographic information system, geo-ontology; closed-world assumption, geo-reasoning,
malaria control.
Volume url; https://wireilla.com/ijbb/vol2.html
PDF URL; https://wireilla.com/papers/ijbb/V2N3/2312ijbb01.pdf